Bluetooth Devices Vulnerable to Hacking
Researchers from Ohio State University have discovered a new vulnerability in devices that use Bluetooth Low Energy (BLE). They found that those mobile apps that use Bluetooth have a design flaw, which leaves them vulnerable to hacking.
After its launch in 2010, BLE has been used in numerous devices. Apple’s iPhone 4s, released in October 2011, was the first smartphone to implement the 4.0 standard. BLE is essentially the smaller version of Bluetooth, but with a different design mechanism. In other words, BLE uses low power and bandwidth, it has a low cost and is easy to operate.
What makes Bluetooth devices vulnerable?
Zhiqiang Lin, associate professor of Computer Science and Engineering at Ohio State University, said that the problem lies in the way Bluetooth devices talk with the mobile apps that control them.
There is a fundamental flaw that leaves these devices vulnerable – first when they are initially paired to a mobile app, and then again when they are operating.
Zhiqiang Lin
Smart devices, such as smart speakers (Amazon Echo), smart doorbells, and wearable fitness trackers (Fitbit) all use BLE. All of these devices require you to install an app on your smartphone. For example, to control your Apple Watch, you need the Watch app on your iPhone.
The devices talk with the apps on your phone by broadcasting a UUID – a universally unique identifier. The identifier allows the apps to recognize the Bluetooth device (e.g. Fitbit). After the broadcast, the connection allows your phone and smart device to talk to one another.
However, the app stores the identifier into its code, otherwise the app won’t be able to recognize the device again. But, Lin’s team found that the storage of UUIDs in apps makes devices vulnerable to a fingerprint attack.
Read Also: Whatsapp Fingerprint Lock – Keep Chats more Secured
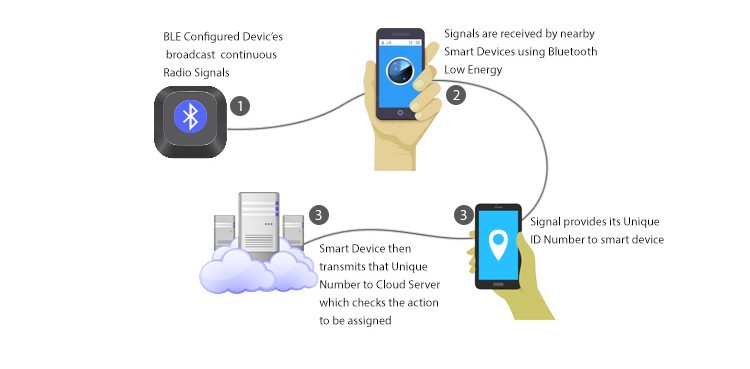
At a minimum, a hacker could determine whether you have a particular Bluetooth device, such as a smart speaker, at your home, by identifying whether or not your smart device is broadcasting the particular UUIDs identified from the corresponding mobile apps.
But in some cases in which no encryption is involved or encryption is used improperly between mobile apps and devices, the attacker would be able to ‘listen in’ on your conversation and collect that data.
Zhiqiang Lin
How widespread is the problem?
After the research team discovered the vulnerability, they wanted to see if the problem is widespread or not. So, they built a “sniffer” – which is basically a hacking program that observes data traveling over a network. The sniffer finds out which devices are using Bluetooth based on the broadcasted UUID.

You May Like: Universal TV Remote Control – Mobile Application
Bluetooth Low Energy design allows the signal to travel over short distances, thus the signal can travel up to 100 meters. Despite that, a hacker can use a receiver or amplifier to find the signal up to 1,000 meters away.
The team put the “sniffer” in a car and drove it around a 1.28-square-mile area near the university’s campus. They found 5,800 BLE devices. From those, 5,500 were identified by an attack and 431 were vulnerable to unauthorized access.
It was in the initial app-level authentication, the initial pairing of the phone app with the device, where that vulnerability existed.
Zhiqiang Lin
According to Lin, if developers tightened defenses in that initial app-level authentication, then the problem could be resolved.
Vulnerable Apps
Lin’s team reported their findings to the developers that created the apps and to the Bluetooth Special Interest Group. They also created a tool that automatically assesses all the apps in the Google Play store. During their research, the tool found 18,166 apps that use BLE. From those, 1,434 were vulnerable apps. Their research does not include apps from the Apple Store.
It was alarming. The potential for privacy invasion is high.
Zhiqiang Lin
These smart devices know a lot of information about us. When even our family members don’t know some of these details. The fitness trackers know the rate of your heart-beat and how many hours you sleep on a given day. The thermostat knows the room temperature you like and warms up the house before your arrival. The speakers that know your daily routine and reads out your to-do list after you get out of bed.
This list can go on and on since new technology is releasing at a very fast rate. Nowadays, all this new tech records our personal information to better cater to our needs. That is why it is important to know when and how our privacy is been violated.
If there are any security issues you want me to write about, please do comment below. Continue to check out Maticstoday for the latest news items, product reviews, security practices, and video game discussions.
Sources: Oreilly, Ohio State News, Help Net Security